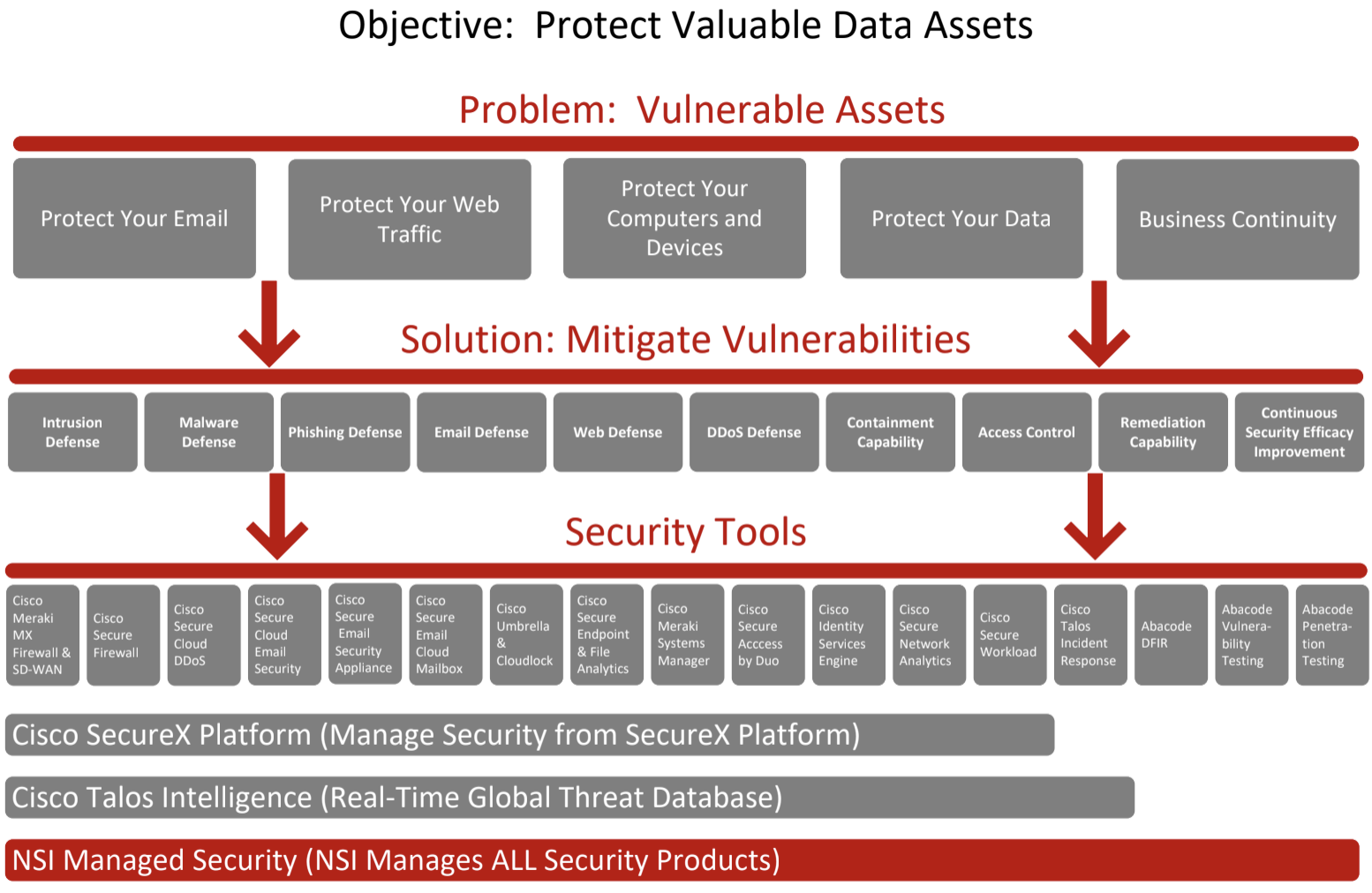
Powerful Protection That Safeguards Your Entire Infrastructure
Finding and maintaining network security solutions can seem overwhelmingly complex. The threat landscape is ever-changing, and attackers find new and creative ways to navigate through security controls. It’s time to take back control over your network security architecture and give your business the protection it needs to thrive.