Building Your Most Efficient Security "Machine"
August 1, 2019 •Steve Tadevich
Jason Dell is the Security Practice Manager at Network Solutions. Today we're going talk to Jason about his job, security, and the best practices and tools to build the most efficient security "machine" possible.
Steve: So Jason, you're the Security Practice Manager. What exactly does that mean? What does a Security Practice Manager do?
Jason: As the Security Practice Manager, my job is to set the standards for the NSI Security Practice. NSI strives to provide the best level of service to our customers. I work with my team to ensure that they are continuously educated to confidently implement security solutions with the industry best practices applied. Rather than just selling security products and services, we partner with our customers by informing and educating, to enable our customers to make good business decisions regarding their security investments.
Steve: I keep hearing this term defense-in-depth. What exactly is defense-in-depth?
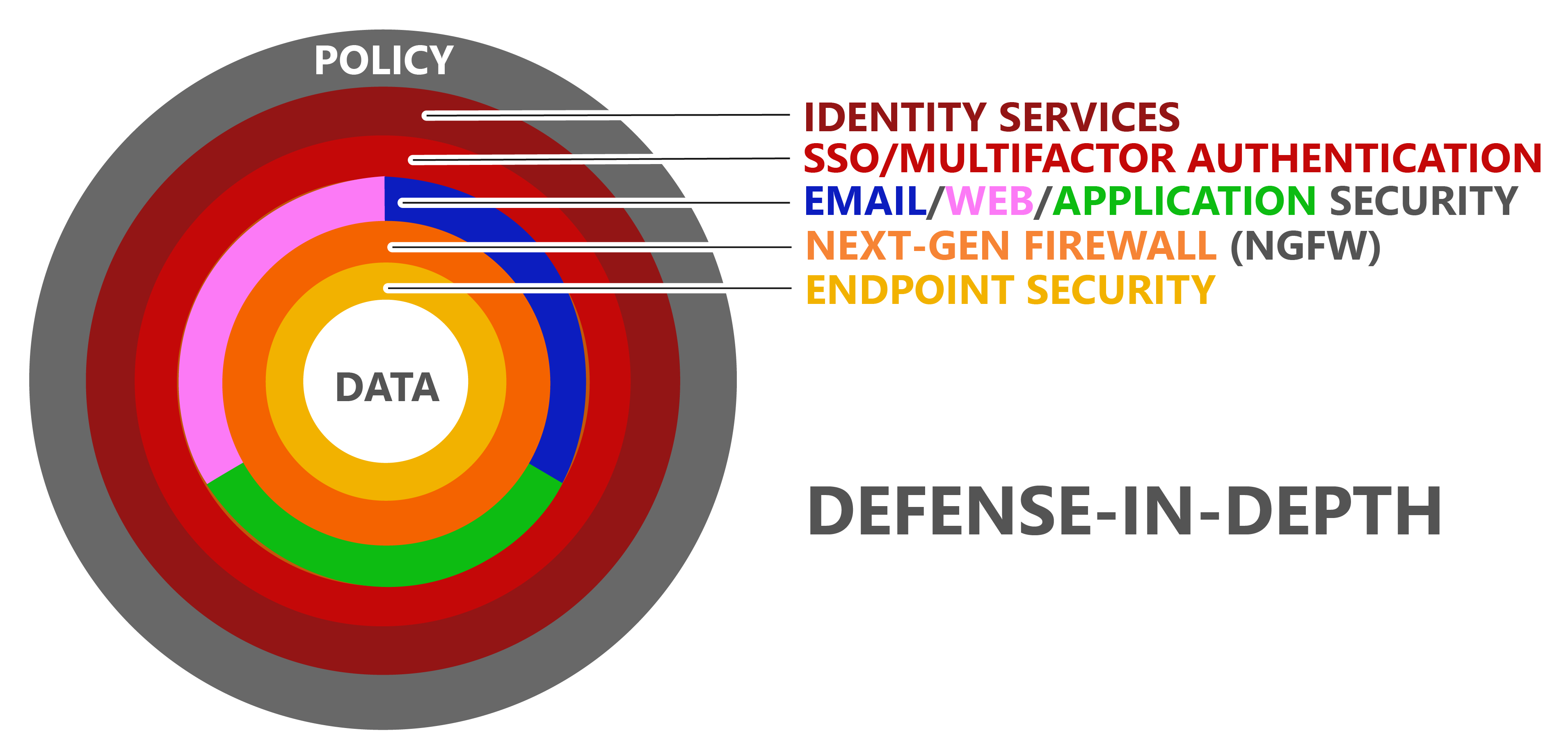
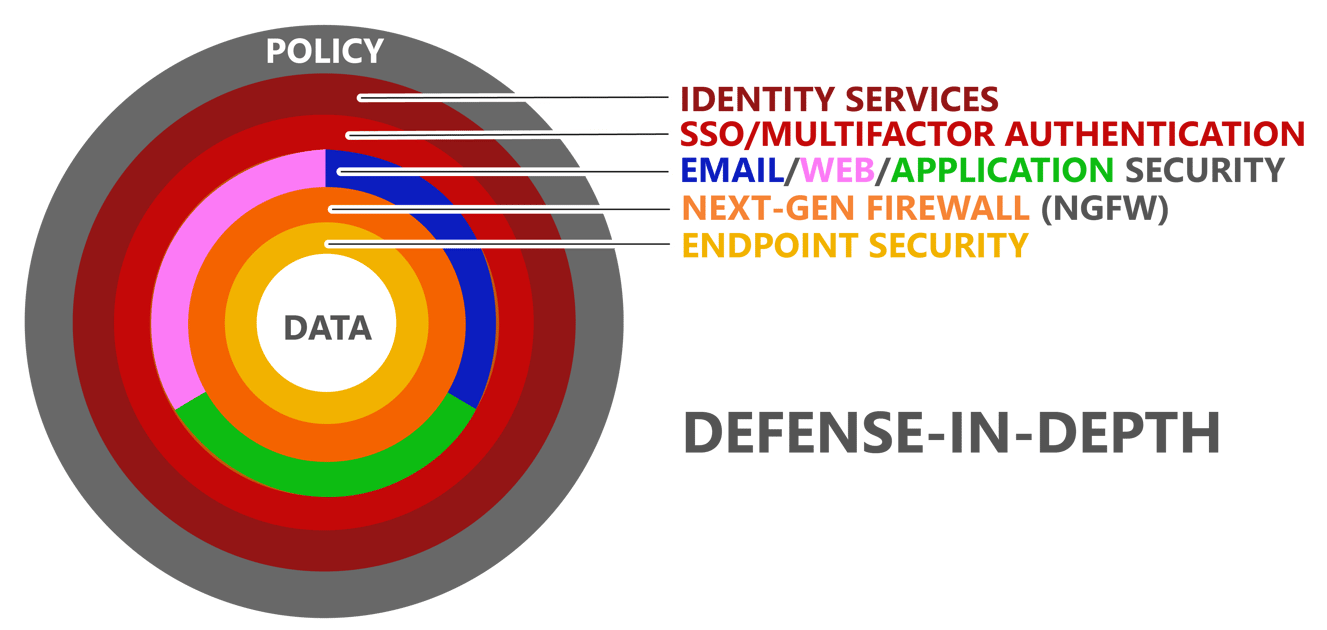
Jason: Defense-in-depth is originally a military term for a tiered defensive line of defenders so that if an attacker penetrates the first line of defense, there is another line of defenders behind it. Within the context of security, it might be an Internet application security solution as the first line of defense. Behind that is a next-generation firewall, and behind that is an endpoint security solution. These security solutions work together as a tiered defense with a sufficient amount of overlap
Steve: Ok, what is Cisco Umbrella?
Jason: Cisco acquired a company called OpenDNS which had been in business for some time. Cisco Umbrella is not just a web security solution, although it does a very good job of web security. Cisco Umbrella is an Internet application security solution. Cisco Umbrella protects any application that accesses the Internet, and which relies on domain name services. Almost every Internet application depends on DNS.
One of the first steps that an Internet application does is to resolve a fully-qualified domain name to a public IP address, which is necessary for traversing the Internet. That's where Cisco Umbrella comes into play. Cisco Umbrella inspects the FQDN and the resolved public IP address. It has the ability to determine whether the request should be blocked due to content policy, or blocked due to the fact that the destination is malicious. If the request is to be blocked, an alternate page is resolved instead, indicating the nature of the blocked request.
But Cisco Umbrella does more than just filter web browser content. Content filtering is content filtering for the most part between different vendors and applications. Cisco Umbrella’s strength is that it has such comprehensive worldwide visibility across the Internet. The Cisco Umbrella threat intelligence database continuously learns and tracks malicious infrastructures worldwide across the Internet by a wide verity of factors. Cisco Umbrella is very effective at being able to determine whether a destination is malicious or not.
Or call 888.247.0900 to schedule your free Umbrella Trial!
Steve: That’s great! So are there any products on the market that compete with Cisco Umbrella?
Jason: Cisco Umbrella is oftentimes implemented to replace traditional web security products, web proxies, or web content filters. But Cisco Umbrella does so much more than that. There are other security technologies that work at the DNS level as well, but they haven't been on the market as long as Cisco Umbrella and they're not as effective at mitigating threats as Cisco Umbrella. The primary key differentiator between Cisco Umbrella and other Internet application products is Cisco Umbrella’s integration with other solutions in the Cisco security suite.
Steve: Okay. So how about AMP for Endpoints? Can you tell me a little bit about that?
Jason: Sure. AMP is an acronym for Advanced Malware Protection. AMP is a security technology with several anti-malware functions working together to mitigate malware. AMP is included as a service across several of Cisco’s security solutions to provide end-to-end and permeating malware mitigation. I could do an entire interview or presentation on AMP alone, but just to summarize it, AMP provides comprehensive and continuous file analysis. In the case of AMP for Endpoints, when a file is introduced to an endpoint the disposition of a file is determined as good, bad, or unknown. Files of “bad” disposition are quarantined. Files of “good” disposition need not be re-evaluated. Files of “unknown” disposition are evaluated in by several other methods.
Steve: What is AMP using to check the file against?
Jason: AMP first checks the disposition of the file using the local cache. If the disposition of the file is not available in the local cache, then an AMP cloud lookup is performed. The AMP cloud is part of the Cisco Talos threat intelligence database. Cisco Talos is a global comprehensive threat intelligence database that is continuously updated by several different security products and services deployed all over the world. So, if the disposition of the file does not exist in the AMP cloud, then the file is sent to Cisco Threat Grid to “detonate” and analyze the file in a sandbox environment to look for indications of compromise. Cisco Threat Grid also compares the structure of the file to other known malware. After analysis, Cisco Threat Grid adds the disposition of this file to the AMP cloud. In the case of Cisco AMP for Endpoints, AMP continuously keeps track of all files on all endpoints, even if the file is renamed. If the disposition of a file changes in the future, AMP has the ability to quarantine malicious files even if they are at rest. This is what Cisco calls retrospective security. No other anti-malware products do this.
Steve: That awesome. So what is ISE?
Jason: Identity Services Engine (ISE) is Cisco's answer to AAA. AAA is an acronym for authentication, authorization, and accounting, and pertains to wired, wireless, and VPN access to a network infrastructure.
The AUTHENTICATION piece determines who and what the endpoint is that is requesting access to the network infrastructure. Authentication may entail requiring user login, and maybe requiring the existence of a trusted certificate, but it can also entail requiring only particular types of endpoints, operating systems, the existence of required software, and many other things.
The AUTHORIZATION piece of AAA determines what network infrastructure resources an authenticated endpoint has access to… what it is allowed to access on the network.
The ACCOUNTING piece of AAA is to track what the endpoint has accessed after authentication. Keeping logs comes in particularly useful in the event of a breach. You need to know how a cybercriminal gained access before you can stop them, and the only way to see how they gained access is by keeping access logs.
To break it down, we can all agree that it is unwise to allow just anyone to wander into your workplace and plug into a network jack and gain access to your production network. But there are many ways to access your network infrastructure and cybercriminals are very resourceful and compromising defenses. All available methods of access need to be secured to ensure that all connection attempts are properly vetted. This is what Cisco ISE does. Cisco ISE is really a Swiss army knife when it comes to AAA. We have talked about the very basics today, but Cisco ISE can go a lot deeper. Cisco ISE can do things like MAC address bypass for devices that cannot authenticate. Cisco ISE can do posture assessments to check a machine to make sure it's running a supported operating system and service packs. Cisco ISE can check for compliance before it provides connectivity. Cisco ISE can provide guest provisioning. Cisco ISE can be integrated with other security products. Once you've defined a machine’s identity, that identity can be reused by other Cisco security solutions to set policy based on that identity.
Steve: Okay. Wow!
I keep hearing the buzz term next-gen firewall or next-generation firewall. What is the difference between a traditional firewall and this fancy new next-gen?
Jason: Traditional firewalls are just “stateful” firewalls. Stateful firewall access lists control traffic based on source address, destination address, and protocols, and that’s pretty much it. Stateful firewalls do not have any deeper visibility into what was going on inside all those protocols. The problem is that most of today's Internet applications run over TCP port 80 and TCP port 443. Vulnerabilities of applications running on those protocols could potentially open the door for cyber-attack.
A Next-Generation Firewall (NGFW) uses deep packet inspection to look inside traffic to identify applications. It can often even see the particular version of each application. An NGFW builds a contextual security database specifically pertaining to the environment where the NGFW is implemented. Cisco NGFW leverages Cisco Talos to know the vulnerabilities of all applications in the contextual security database and uses this information to tune the intrusion prevention capabilities of the NGFW to keep it efficient and up to date.
Cisco NGFW also provides malware protection with AMP technology, and URL filtering as well. Cisco NGFW also provides DNS level security, and IP and FQDN-level security intelligence, leveraging Cisco Talos.
Steve: I lead you down this road because this is a common question we get from customers . “Why do I need an AMP for Endpoints AND an AMP license for my next-gen firewall?”
Jason: That is a great question. As I mentioned before AMP is a technology that is integrated across several Cisco security solutions. There is Cisco AMP for Endpoints, Cisco AMP for NGFW, Cisco AMP for Integrated Services Routers, Cisco AMP for Web Security Appliance, Cisco AMP for Email Security Appliance, Cisco AMP for Cloud Email Security, AMP is available on Meraki MX, and AMP is integrated in Cisco Umbrella.
Pertaining to your specific question, Cisco AMP for Endpoints is the most fully-featured and effective AMP-enabled product for mitigating malware threats. Cisco AMP on NGFW does some of the things that Cisco AMP for Endpoints can do but it does not to some other things that just don't make sense to do on a firewall, like device trajectory.
Cisco AMP for Endpoints can be installed on Windows, macOS, CentOS, RedHat, IOS, and Android. Cisco AMP for endpoints is not an option for IoT devices or endpoints with operating systems. In this case, NGFW is used to protect these endpoints from malware.
Steve: Another recent question. Which firewall should I buy for our environment? It depends, right?
Jason: Exactly. It depends on the needs. The Next-Generation firewall provides the most fully-featured security controls. An NGFW is much more customizable and has the ability to provide much more granular control. An NGFW learns an environment and it adapts to it. An NGFW provides several charts for visibility. An NGFW can be tuned and then left to work on its own, but it is most effective when anything that it considers as a potential threat is fully investigated. Of course, that requires an employee with the time and skill to do that.
A company with a small IT staff with limited time available for threat-hunting may choose instead to go with Meraki MX. The Meraki MX includes the same “stateful” firewall capabilities and does provide application visibility and control. The MX includes Sourcefire IPS with limited aggressiveness settings. It includes AMP with a binary “on” or “off” setting. So, the Meraki MX provides these features, but they cannot be tuned specifically to the environment.
Another reason why Meraki MX may be the right choice is if other Meraki gear exists in the environment. If the environment contains Meraki switches, Meraki access points, and Meraki firewall, then there is one dashboard to manage all of these components.
Steve: What is Duo?
Jason: Duo Security is a recent Cisco acquisition. Multi-factor authentication (MFA) is what most people know Duo for. Consider this: without MFA, when authenticating to an application, or a service, or an appliance, or a workstation, only a username and a password is required for access. That’s all good and fine until somebody compromises these credentials. A phished set of credentials potentially gives cybercriminals the keys to the kingdom.
Duo provides a second factor of authentication. Username and password and the second factor of authentication is required for access. The most common method for MFA for that is an app that runs on a smartphone that notifies with something like, “I see you just logged in. Is this you?” In these cases, “Approve” must be clicked on the app in order to provide access.
If a notification is received this out of the blue, when the Duo app asks, “Is this you?” clicking “No” would reject access and indicate that it is time to change the password.
In addition to MFA, Duo provides single sign-on for several native apps and for any SAML2-capable application. It's getting more and more difficult nowadays to manage multiple passwords. We hear the experts say to have these long passwords, and not to reuse passwords between applications. Most people have several different cloud applications and systems they access and they’re having difficulty remembering all of these long passwords. Single sign-on comes into play for applications and services and systems that are compatible with single sign-on. Then you each user has only one set of credentials (or at least a reduced total number of passwords to remember). With Dou, MFA is built into SSO.
Steve: So how do all these disparate, or seemingly disparate security products that we've talked about all work together to create a complete Security solution?
Jason: Cisco security products are getting less and less disparate as time goes by. Security products should work like cogs in a machine where they depend on each other to work as a security system. If one decides to go with a best-of-breed security approach, one cog might not match directly with the cog next to it. For example, how is information between security components? There is contextual security information that should be passed between these different components to help all security components work the most effectively.
Cisco designs their applications to share that information between their products, so they all work together as a security system. Let’s say that a company has Cisco ISE implemented to controls network infrastructure access. As well, this same company has Cisco Stealthwatch to monitor for and alert on anomalous traffic on the network. If Stealthwatch detects potentially malicious traffic sourced from a particular endpoint, Stealthwatch can communicate with Cisco ISE, which can them sequester this endpoint into a remediation segment. That is two cogs in the security machine. Cisco Next-Generation Firewall can pass contextual security information to Cisco ISE. Cisco AMP for Endpoints can integrate with Cisco Next-Generation Firewall so that a firewall can be seen in file trajectory.
A new integration tool that Cisco provides is called Cisco Threat Response. Cisco Threat Response integrates several Cisco security products into a single dashboard that can be used to search for potential threats by indications of compromise. Cisco Threat Response is not a purchased product. It comes free with Cisco AMP for Endpoints, Cisco Umbrella, Cisco Email Security or Cisco Threat Grid.
Steve: Okay, you've answered a lot of questions today. The last question. Can my network be 100% secure?
Jason: Any security engineer, security analyst, or security vendor, if they're being honest with will never state that threats can be eliminated. But threats can be mitigated. The importance now is in the efficacy of the security system. Higher security system efficacy means higher threat mitigation, which means minimizing risk to critical data assets.
A security system, all of the security products, and security policies need to be evaluated for efficacy periodically for relevancy. As applications and services mature, new features come out that may change the way they work. Last year's best practices may be different than this year's best practices.
Consider also that an effective security system is not just comprised of security products. Having a relevant written security policy that your employees agree to also mitigates risk. Having a breach remediation plan in place will minimize scrambling to try to figure out what to do during a breach. This could potentially reduce the impact of a breach. Have a disaster recovery plan in place that covers what to do if there is a fire, or a flood, or any of the other many things that can be considered a disaster.
So, can we eliminate threats? No. Threats are moving targets. But evaluating the efficacy of a security system and all of its components will reduce risk as much as possible.

Get Updates
Featured Articles
Categories
- AI (18)
- Automated Technology (9)
- backup (1)
- Cisco (29)
- Cisco Live Update (1)
- Cisco News (2)
- Cisco UCS (1)
- Cloud Networking (4)
- Collaboration (26)
- compute (1)
- CyberSecurity (34)
- Data Center (32)
- Defense (1)
- DevOps (3)
- DisasterRecovery (1)
- DNA (2)
- Education (3)
- Encryption (1)
- Enterprise Networking (32)
- Full-Stack (1)
- Future (1)
- healthcare (2)
- hybrid cloud (1)
- Innovative Technology (12)
- Internet of Things (2)
- IoT (2)
- Managed Services (11)
- Manufacturing (1)
- Modern Data Center (2)
- Monitoring (2)
- Network Management (4)
- Networking (2)
- NSI (1)
- nutanix (1)
- Observability (1)
- OT (1)
- Ransomware (2)
- SchoolTechnology (6)
- SD-WAN (1)
- SDN (1)
- securit (1)
- Security (73)
- security management (4)
- security strategy (8)
- SSE (1)
- sustainability (1)
- Telehealth (4)
- Telemedicine (1)
- veeam (1)
- Video (1)
- videoconferencing (1)
- Virtualization (2)
- webex (3)
- XDR (1)
- Zero Trust (8)