Blog
Can You Afford a Cybersecurity Attack?
January 20, 2026 •Jason Dell
Duo — The First Frontier of Enterprise Security
January 12, 2026 •John Salmon
Cybersecurity in 2026: What’s Changed and What’s Next
January 2, 2026 •Jason Dell
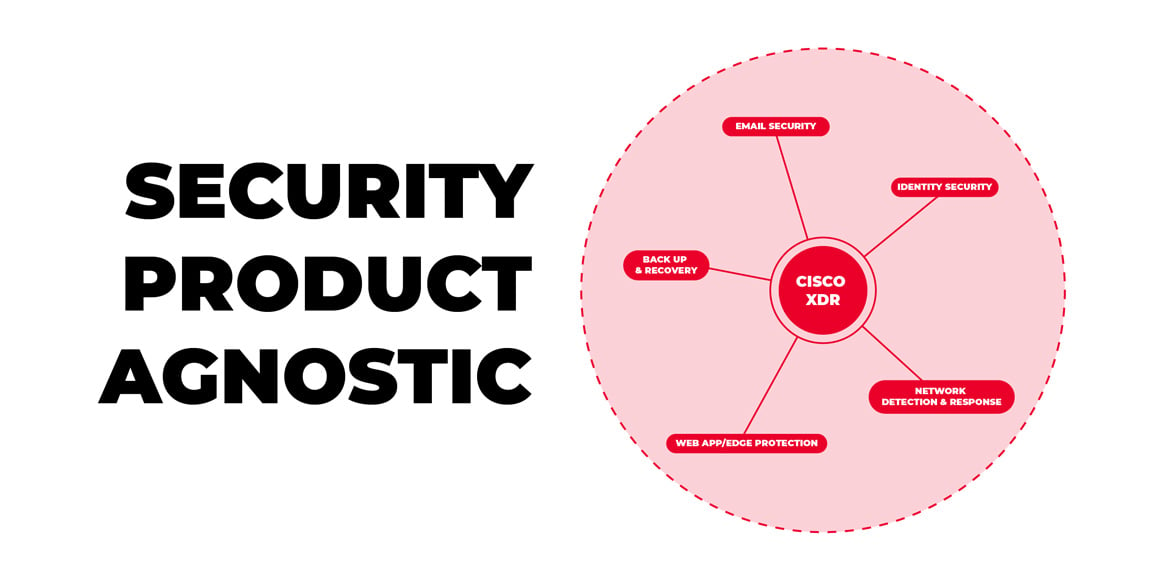
Cisco XDR: the “universal adapter” your SOC didn’t know it had
November 18, 2025 •Network Solutions
Cisco Partner Summit 2025: Key Announcements from San Diego
November 11, 2025 •Network Solutions