Cisco XDR: the “universal adapter” your SOC didn’t know it had
November 18, 2025 •Network Solutions
7minute read
Most security teams run a patchwork of tools: an EDR from one vendor, firewalls from another, cloud detectors from a third, identity controls somewhere else, and a SIEM to stitch the story together. Then an incident hits, and analysts are tab switching, pasting indicators, and trying to remember which console isolates a host versus disables a user.
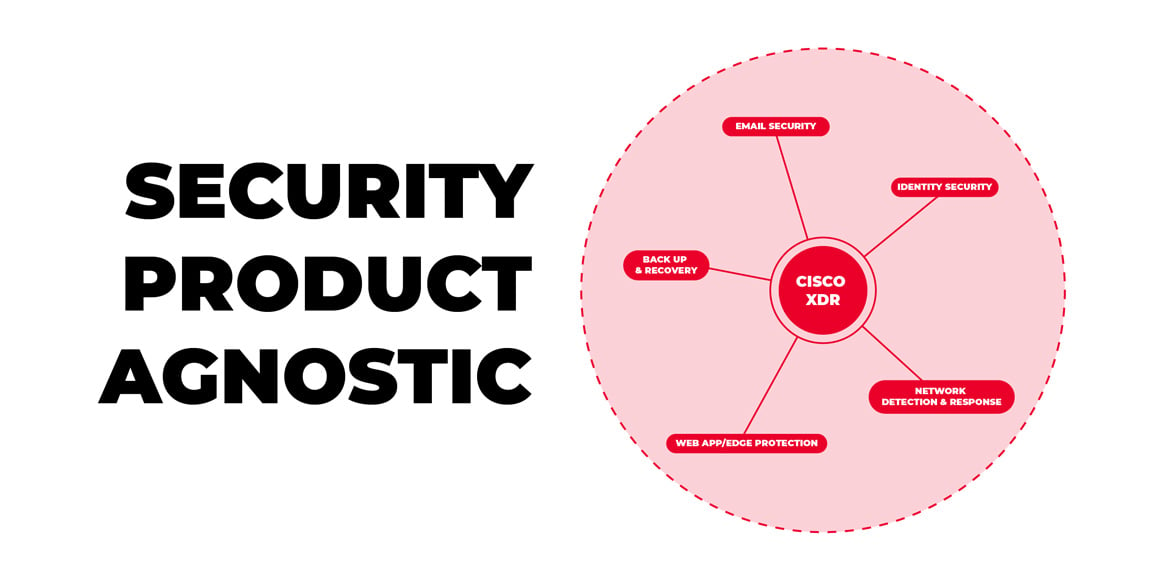
Cisco XDR is designed to short-circuit swivel chair fatigue. It isn’t just “Cisco for Cisco.” It’s deliberately brand agnostic: it ingests detections from many vendors, enriches them, correlates them into incidents, and—crucially—can act across those third-party tools from a single place. Think of it as a universal adapter for your SOC: one plug that fits the messy reality of mixed vendor security stacks. (Cisco)
What Cisco XDR is (and what it isn’t)
XDR in a sentence. Extended Detection and Response brings together telemetry across endpoints, network, email, identity, cloud, and more, then performs analytics and guided response to collapse time-to-verify and time-to-contain. Cisco’s data sheet highlights native correlation across those domains, an Attack Storyboard with instant attack verification, and embedded forensics to gather evidence and take targeted actions. (Cisco)
Not a SIEM, not a SOAR. XDR correlates security events and drives response, but it doesn’t replace a SIEM’s broad log management, compliance reporting, or “search anything for years” use cases. Cisco XDR even integrates with Splunk (and other SIEMs) to pull reputations, sightings, and context into investigations. In other words: keep your SIEM; let XDR accelerate detection and response on top. (Cisco)
Brand agnostic by design
Cisco publishes a living catalog of third-party integrations (and what each one can do), covering EDRs, firewalls, email gateways, cloud services, identity providers, ITSM tools, and more. The official capabilities matrix shows, for example, integrations with Microsoft Defender for Endpoint/Office 365, CrowdStrike Falcon, Sentinel One, Palo Alto Cortex XDR/Firewalls, ServiceNow, Google Cloud, Sumo Logic, PagerDuty, Slack, and many others—each marked for the exact mix of detection, hunting, asset context, and response automation supported. (Cisco XDR Documentation)
A few concrete examples:
- Microsoft Defender for Endpoint. From Cisco XDR you can ingest Defender detections, hunt across its telemetry, and isolate hosts or block observables (hashes, IPs, domains, URLs, certs) as a response—no console-jumping required. (Cisco XDR Documentation)
- Palo Alto Cortex XDR & Firewalls. Cisco XDR can query Cortex XDR detections, contribute sightings to incidents, and target Cortex via automation; Cortexfed NGFW alerts can be queried via API as well. (Cisco XDR Documentation)
- CrowdStrike Falcon. Falcon detections enrich Cisco XDR incidents and enable rapid response actions from within XDR, plus device inventory context when triaging. (Cisco XDR Documentation)
- ServiceNow. Use prebuilt workflows/playbooks to create incidents and change tickets as part of an automated response flow. (Cisco XDR Documentation)
Cisco keeps adding to this “open ecosystem” and emphasizes vendor agnostic operation and standards based data exchange in public posts and event summaries. (Cisco Blogs)
How it works: the “universal adapter” architecture
Several design choices make Cisco XDR feel like that single adapter that plugs into many brands:
- Common schemas & models. Under the hood, Cisco uses the Cisco Threat Intelligence Model (CTIM) to structure relationships and context, and it supports the open OCSF (Open Cybersecurity Schema Framework) for normalized analytics queries. This lets XDR ask consistent questions across different vendors’ data. (Cisco DevNet)
- Incidents, not alert buckets. XDR correlates alerts and events into prioritized incidents, adds Talos threat intelligence and asset context, and surfaces a guided response path—so analysts work one narrative instead of dozens of siloed alerts. (Cisco)
- Pivot Menu & Atomic Actions. From any observable (hash, IP, user, hostname), the Pivot Menu exposes actions in the connected tools; Atomic Actions are reusable building blocks for lowcode workflows. Together, they make cross product operations feel native. (Cisco XDR Documentation)
- Targets & Playbooks. When you add an integration, XDR auto creates a target for automation, so playbooks can call that product’s API safely (for example, “disable a Microsoft Entra user”). (Cisco XDR Documentation)
- Forensics built in. XDR Forensics can collect hundreds of artifact types and launch a remote shell to speed triage and eradication—all from the incident pane. (Note: shell use respects endpoint isolation controls.) (Cisco)
What you can manage across third-party tools
“Manage” in this context means investigate and take response actions without leaving XDR, driven by normalized data and automation. Typical cross vendor actions you can centralize include:
- Endpoint containment: isolate a host in Microsoft Defender for Endpoint or CrowdStrike during containment. (Cisco XDR Documentation)
- Identity controls: disable or reenable a user in Microsoft Entra ID as part of a phishing or credential theft playbook. (Cisco XDR Connect)
- Firewall & network response: query third-party NGFW alerts (e.g., Palo Alto), and feed enriched context back into your incident to drive blocks or segmentation via automation. (Cisco XDR Documentation)
- Ticketing & comms: open ServiceNow incidents/changes, page responders in PagerDuty, or post updates to Slack—all orchestrated by XDR playbooks. (Cisco XDR Documentation)
- SIEM lookups: reach into Splunk (or other SIEMs) during an investigation to pull sightings/reputations without tab switching. (Cisco)
Because these are API backed integrations, response depth matches what that vendor exposes (and what you permit via scopes/permissions). The result: analysts stay in one console while XDR talks to the right product behind the scenes. (Cisco XDR Documentation)
Why teams miss the “universal adapter” idea
Many assume “XDR = single vendor lockin.” Cisco’s approach flips that: third-party telemetry and controls are first-class citizens, and Cisco even documents which integrations require which tier and what they can contribute—detection, asset context, dashboard cards, controls and responses, or automation only. That transparency makes it clearer how far you can manage each nonCisco tool from inside XDR. (Cisco XDR Documentation)
Under the covers, the common data models (CTIM/OCSF) and automation exchange help hide vendor quirks so you can build repeatable playbooks that work regardless of brand—exactly what a universal adapter is supposed to do. (Cisco DevNet)
Capabilities you’ll care about
- Correlation & prioritization across vendors. XDR correlates endpoint, network, firewall, email, identity, DNS, and cloud signals—reducing false positives and presenting one prioritized incident to investigate. (Cisco)
- Drag and drop automation. A low to no code editor plus hundreds of built-in Atomic Actions and installable workflows in Cisco XDR Connect help you build cross tool playbooks in minutes. (Cisco XDR Documentation)
- Agentic AI assistance. Cisco has introduced agentic AI to accelerate verification and investigation across XDR (and Splunk), aiming to auto validate attacks and propose next steps. (Dark Reading)
- Embedded forensics. Collect artifacts and remote shell into impacted endpoints from the incident view to speed containment and eradication. (Cisco)
The fine print: real limitations to understand
Being universal has tradeoffs. These are the ones seasoned teams plan for:
- It doesn’t replace your SIEM. Use XDR to act fast on security relevant telemetry; use your SIEM for broad log ingestion, compliance reporting, and long-term hunting. Cisco even treats SIEMs as data/context sources during investigations. (Cisco)
- Data retention & ingest limits. Cisco XDR includes 90 days of data retention by default and 2 GB/user/month of data ingestion (with options to purchase more or extend retention). SIEM scale log archiving is intentionally not the goal. (Cisco)
- Depth varies by integration. Cisco’s matrix shows some products support full controls and responses, others provide detections and context only, and legacy integrations may work but aren’t officially supported. Check the table before you assume a given action exists. (Cisco XDR Documentation)
- APIs and permissions matter. To get full functionality, you must grant the right scopes and complete all steps; if a third-party API changes, some automations may need updates—a risk Cisco itself flags in its buyer’s guide. (Cisco XDR Documentation)
- Licensing gates third-party control. Threat intel and ITSM integrations are included with Essentials, but most third-party security tool integrations (EDR/NGFW/Cloud/IDP) require Advantage (or Premier for managed service). (Cisco XDR Documentation)
- Endpoint shell & isolation interplay. Remote shell in XDR Forensics can be blocked by isolation policies (Cisco’s or another vendor’s) — expected, but important to plan around in playbooks. (Cisco XDR Documentation)
A quick blueprint to use Cisco XDR like a universal adapter
- Start with your “must talk to” tools. Add Microsoft Defender (endpoint + O365), your nonCisco EDR (CrowdStrike/SentinelOne), your firewall platform (e.g., Palo Alto via Cortex), identity (Microsoft Entra ID), and ITSM (ServiceNow). Verify which support controls and responses. (Cisco XDR Documentation)
- Normalize your hunting. Use the Investigate view plus OCSF backed queries to ask the same questions across vendors (for example, “Where has this hash been seen?”). (Cisco XDR Connect)
- Encode your playbooks. Build low code workflows for your top three incident types (phishing, credential theft, malware). Include steps like isolate device (Defender) → disable user (Entra) → open ServiceNow → notify Slack. Reuse Atomic Actions wherever possible. (Cisco XDR Documentation)
- Close the loop with forensics. Add “collect artifacts” and (where allowed) remote shell to speed eradication and evidence handling. (Cisco)
- Keep an eye on ingest/retention. Decide what telemetry truly needs to land in XDR versus staying primarily in the SIEM, and purchase extra ingest/retention if your use case demands it. (Cisco)
Bottom line
Cisco XDR earns the “universal adapter” label because it embraces, rather than fights, mixed vendor environments. It correlates detections into clear incidents, layers on threat intel and asset context, and lets you pull the right third party levers—isolate that Defender host, disable that Entra user, open that ServiceNow ticket—without leaving one console.
It won’t replace your SIEM, and you should verify the exact response depth per integration (and plan for permissions and API changes). But if your goal is faster verification and containment across a heterogeneous stack, Cisco XDR’s open ecosystem, standards alignment (CTIM/OCSF), and low code automation make it the plug that finally fits the whole drawer of adapters your SOC has been juggling. (Cisco)
Learn more about Network Solutions at https://www.nsi1.com/solutions-security. Talk to our security experts at NSI by calling (888) 247-0900, email info@nsi1.com to get started, or schedule to talk with us below!
Sources & further reading
- Cisco XDR Data Sheet – capabilities, license tiers, SIEM integrations, ingest & retention. (Cisco)
- Cisco’s third-party integrations & capabilities matrix – which vendors support detections, asset context, controls, automation. (Cisco XDR Documentation)
- Microsoft Defender for Endpoint integration – example of third-party response (host isolation, blocking). (Cisco XDR Documentation)
- Palo Alto Cortex XDR / Firewalls integrations – third-party EDR/NGFW telemetry and automation targets. (Cisco XDR Documentation)
- CrowdStrike Falcon integration – detections, context, and rapid response from inside XDR. (Cisco XDR Documentation)
- Automation & workflows – Pivot Menu, Atomic Actions, low code editor, and XDR Connect catalog. (Cisco XDR Documentation)
- Open ecosystem & standards – Cisco’s vendor agnostic stance and OCSF alignment. (Cisco Blogs)
Get Updates
Featured Articles
Categories
- AI (19)
- Automated Technology (10)
- backup (1)
- Cisco (33)
- Cisco Live Update (1)
- Cisco News (2)
- Cisco UCS (1)
- Cloud Networking (5)
- Collaboration (26)
- compute (1)
- CyberSecurity (36)
- Data Center (33)
- Defense (1)
- DevOps (3)
- DisasterRecovery (1)
- DNA (2)
- Education (3)
- Encryption (1)
- Enterprise Networking (34)
- Full-Stack (1)
- Future (1)
- healthcare (2)
- hybrid cloud (1)
- Hybrid Cloud Strategy (1)
- Hyperconverged Infrastructure (1)
- Infrastructure Cost Optimization (1)
- Innovation (1)
- Innovative Technology (12)
- Internet of Things (2)
- IoT (2)
- Managed Services (11)
- Manufacturing (1)
- Modern Data Center (2)
- Monitoring (2)
- Network Management (4)
- Networking (3)
- NSI (1)
- nutanix (1)
- Observability (1)
- OT (1)
- Ransomware (2)
- SchoolTechnology (6)
- SD-WAN (1)
- SDN (1)
- securit (1)
- Security (77)
- security management (6)
- security strategy (9)
- SSE (2)
- sustainability (1)
- Telehealth (4)
- Telemedicine (1)
- veeam (1)
- Video (1)
- videoconferencing (1)
- Virtualization (2)
- VMware to Nutanix (1)
- webex (3)
- wifi (1)
- XDR (1)
- Zero Trust (8)



