Mitigating One of the Biggest Threats: Web
February 21, 2019 •Jason Dell

Web and email have long been the top two threat vectors. Today we will address web security. Web security involves web application content filtering, sometimes with antivirus capability. This is a very important security control to consider for your organization to mitigate threats.
Often, web security involves the use of a proxy server, especially if you intend to inspect SSL-encrypted traffic. 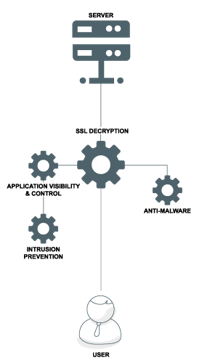 However, there are several caveats to using a proxy. Certain web sites just will not cooperate with a proxy. These sites need to be added to a proxy bypass list. SSL decryption is particularly susceptible to proxy incompatibility. These sites need to be exempt from SSL decryption, or even added to the proxy bypass list. Confidentiality/compliance may be of concern regarding SSL decryption. These sites or even categories may need to be except from SSL decryption.
However, there are several caveats to using a proxy. Certain web sites just will not cooperate with a proxy. These sites need to be added to a proxy bypass list. SSL decryption is particularly susceptible to proxy incompatibility. These sites need to be exempt from SSL decryption, or even added to the proxy bypass list. Confidentiality/compliance may be of concern regarding SSL decryption. These sites or even categories may need to be except from SSL decryption.
Constantly maintaining proxy bypass and SSL exceptions is burdensome and tends to lead to “configuration sprawl” and losing control of what is valid configuration. Not to mention the frustration of users who have to continuously request that troublesome sites be investigated. Most importantly, if a site is bypassed, it is not inspected for threats. So multiple holes are poked into your web security solution, potentially permitting threats though unchecked.
Web security products are often categorized as Secure Web Gateways (SWG). Products in this category protect web traffic, and web traffic alone. Cisco Umbrella is categorized as a Secure Internet Gateway (SIG). Cisco Umbrella includes the same web security features as a SWG, but extends the threat mitigation to ALL Internet applications, not just web pages. This provides a much broader range of protection. In addition, a proxy bypass list does not need to be maintained, and SSL can be intelligently inspected.
Here is how Cisco Umbrella works:
Nearly every Internet application relies on Domain Name Services (DNS) to resolve a fully-qualified domain name (FQDN) to an IP address. Most organizations maintain their own private DNS servers to resolve internal FQDNs, and then forward external FQDNs to public DNS servers, or to DNS servers provided by the Internet Service Provider. Cisco Umbrella provides public DNS servers that anyone can use for free for public FQDN name resolution. The Cisco Umbrella servers are even faster than other public DNS servers.
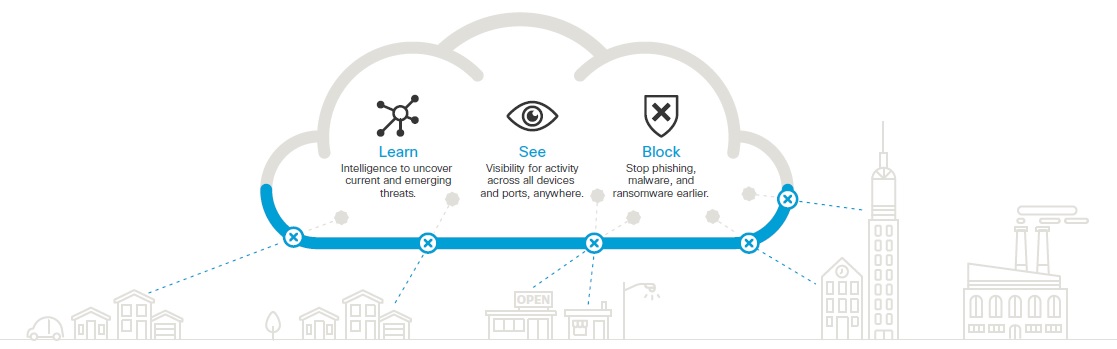
If an organization is a Cisco Umbrella subscriber, then DNS queries are compared to a configured Umbrella policy. If the requested destination is permitted by policy, then the destination IP address of the FQDN is returned. If requested destination is denied by policy, then the user is instead returned the IP address of a web page that explains the policy violation. Non-browser Internet applications are simply given an IP address that prevents the offending access to the offending Internet destination. Since name resolution occurs before any data is transmitted, security checks are done before data is transmitted, rather than catching threats in transit. This makes Cisco Umbrella an efficient Internet application solution.
Going a little deeper, if Cisco Umbrella Active Directory integration is enabled, then other attributes such as username and group membership are encrypted and sent with the DNS query to Cisco Umbrella. Now, policy based on AD username or AD group membership can be applied. As well, now the Umbrella dashboard has the ability to show username in reports.
Cisco Umbrella also includes a roaming client for Windows and Mac. This means that your users can either have the same policy that users would use if they were onsite, or they may have a policy specifically for roaming users. This provides flexibility and increased visibility.
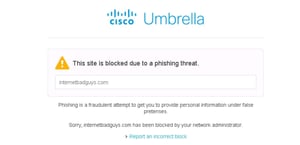 In addition to content settings, Cisco Umbrella provides a rich variety of threat mitigation option that can be customized per policy. Included in the security settings are malware, newly seen domains, command and control callbacks, phishing attacks, dynamic DNS, potentially harmful domains, DNS tunneling VPN, and cryptomining. An entire blog post could be dedicate to explaining the security intelligence behind how Cisco Umbrella mitigates threats.
In addition to content settings, Cisco Umbrella provides a rich variety of threat mitigation option that can be customized per policy. Included in the security settings are malware, newly seen domains, command and control callbacks, phishing attacks, dynamic DNS, potentially harmful domains, DNS tunneling VPN, and cryptomining. An entire blog post could be dedicate to explaining the security intelligence behind how Cisco Umbrella mitigates threats.
Now, some domains host several sites, some sites may be benign, some sites may be malicious. You don’t want to block an entire domain, including the benign sites, just to block the malicious sites. Cisco Umbrella is aware of these domains. For requested sites within one of these domains, Cisco Umbrella will utilize the Intelligent Proxy to provide deeper inspection and more granular control. Don’t be put off by the word “proxy” in this instance. There are no proxy bypass lists to maintain. Cisco Umbrella handles it all transparently and seamlessly. Advanced Malware Protection inspection can be enabled for sites that are Intelligent Proxy eligible. Yes, the same Cisco Advanced Malware Protection technology that is the core of AMP for Endpoints and AMP for Networks.
To go further, SSL inspection is available for sites that are Intelligent Proxy eligible. Again, there is no need for an SSL bypass to handle per-site exceptions for functionality purposes. SSL inspection will ONLY occur for sites that are Intelligent Proxy eligible. For compliancy, you can choose to easily create a list of categories to exempt from SSL decryption, so traffic to those destinations stays encrypted and confidential.
Finally, Cisco Umbrella has a comprehensive and growing list of cloud applications that are evaluated by risk and can be systematically blocked per policy.
In summary, with Cisco Umbrella, you have all of the protection that you have with a traditional SIG, plus protection for ALL Internet applications, and without the risk or burden of maintaining bypass lists. In addition, you have more granular control with unmatched threat mitigation.
For more information on Cisco Umbrella, schedule a short conversation below! We are here to help.
Get Updates
Featured Articles
Categories
- AI (18)
- Automated Technology (9)
- backup (1)
- Cisco (29)
- Cisco Live Update (1)
- Cisco News (2)
- Cisco UCS (1)
- Cloud Networking (4)
- Collaboration (26)
- compute (1)
- CyberSecurity (34)
- Data Center (32)
- Defense (1)
- DevOps (3)
- DisasterRecovery (1)
- DNA (2)
- Education (3)
- Encryption (1)
- Enterprise Networking (32)
- Full-Stack (1)
- Future (1)
- healthcare (2)
- hybrid cloud (1)
- Innovative Technology (12)
- Internet of Things (2)
- IoT (2)
- Managed Services (11)
- Manufacturing (1)
- Modern Data Center (2)
- Monitoring (2)
- Network Management (4)
- Networking (2)
- NSI (1)
- nutanix (1)
- Observability (1)
- OT (1)
- Ransomware (2)
- SchoolTechnology (6)
- SD-WAN (1)
- SDN (1)
- securit (1)
- Security (73)
- security management (4)
- security strategy (8)
- SSE (1)
- sustainability (1)
- Telehealth (4)
- Telemedicine (1)
- veeam (1)
- Video (1)
- videoconferencing (1)
- Virtualization (2)
- webex (3)
- XDR (1)
- Zero Trust (8)



