Encrypted Traffic Analysis: How to Find Hackers Where They Hide
December 7, 2017 •Network Solutions

Encryption has been around for years now and has become an ally and enemy of security professionals. Data encryption used to be an after thought but now it is at the forefront of any CIO’s security strategy. Why has this become such a necessity? Hackers.
 All security strategies should be agile and adapt to the changing threat environment – even if it’s not in the budget. According to a study done by McAfee, small businesses are set to lose $2 Trillion a year to ransomware, DDOS attacks, and malware intrusions by 2019.
All security strategies should be agile and adapt to the changing threat environment – even if it’s not in the budget. According to a study done by McAfee, small businesses are set to lose $2 Trillion a year to ransomware, DDOS attacks, and malware intrusions by 2019.
Now you’re asking yourself – How do I keep up with hackers who have no lives and just want to ruin my business? There are a couple things you can do. You can protect your DNS layer, gate off access to certain personnel through permissions or gain visibility into who is going where on your network.One of the most interesting advancements involves the packets of data themselves. Since the release of the
Advanced Encryption Standard (AES) in 2001, data encryption has become more sophisticated and refined. This is a good and a bad thing. The upside is that everyday data can be encrypted and decrypted quickly with a set standard. The bad being that hackers can hide their malware and ransomware deeper than ever before – only to be released when decrypted. It isn’t feasible to perform deep-packet inspection on every lick of
data so catching advanced attacks is becoming harder by the day.
Encrypted Traffic Analysis
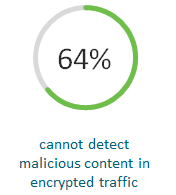
Gartner predicts that 80% of web traffic will be encrypted by 2019 which makes finding out what’s in data packets harder and riskier.
What is Encrypted Traffic Analysis (ETA)?
ETA is the ability to see inside data packets without decrypting them. What are they carrying? Is it benign or malicious? With typical packet inspection, encrypted data had to be unpacked and looked inside – weather known or unknown – before being passed through to the final destination.
This creates a multitude of problems but the biggest problem is the decrypt/encrypt process that has to take place to see inside the data packet This process slows down data flow and can make applications run extremely slow.
ETA aims to solve this problem by passive monitoring, the extraction of data elements and supervised machine learning that comes together to give a picture of what the data packet is up to.
How does this make me more secure if you aren’t decrypting the traffic?
ETA uses certain elements of a data packet to determine whether the nature is benign or malicious.
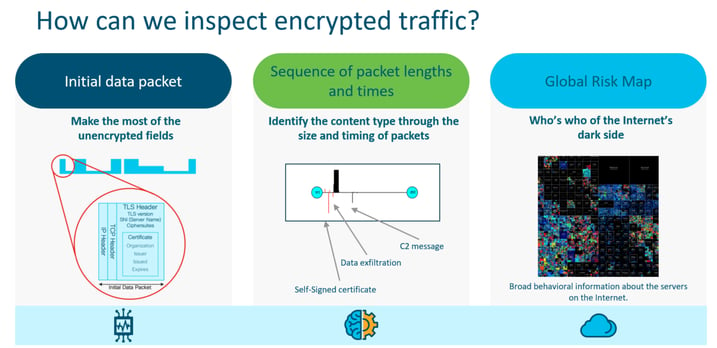
These elements, combined with machine learning, tell the story of the data packet and are able to give the firewall a better understanding of where, when and why something is coming onto the network. These elements reinforce one another inside the analytics engine. Using cognitive analytics, all these elements are able to learn from one another and improve upon speed of detection and security. It’s like having an Alexa for your network.
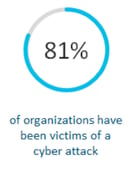
The ability to check for viruses in encrypted traffic is something new to the market and will be a staple in any enterprise network within the next few years. I know what you’re thinking – How accurate can it really be? A real-world experiment based on real data achieved a 99% accuracy with a 0.01% false positives. Those are powerful numbers!
Currently, Cisco is the only market player that is offering ETA with a security portfolio that is equipped to handle it. With this kind of technology, your security portfolio needs to be working in tandem with one another so they can communicate threat assessments and keep your network safe every step of the way.
Be on the lookout for more about Encrypted Traffic Analysis (ETA)!
Get Updates
Featured Articles
Categories
- AI (19)
- Automated Technology (10)
- backup (1)
- Cisco (33)
- Cisco Live Update (1)
- Cisco News (2)
- Cisco UCS (1)
- Cloud Networking (5)
- Collaboration (26)
- compute (1)
- CyberSecurity (36)
- Data Center (33)
- Defense (1)
- DevOps (3)
- DisasterRecovery (1)
- DNA (2)
- Education (3)
- Encryption (1)
- Enterprise Networking (34)
- Full-Stack (1)
- Future (1)
- healthcare (2)
- hybrid cloud (1)
- Hybrid Cloud Strategy (1)
- Hyperconverged Infrastructure (1)
- Infrastructure Cost Optimization (1)
- Innovation (1)
- Innovative Technology (12)
- Internet of Things (2)
- IoT (2)
- Managed Services (11)
- Manufacturing (1)
- Modern Data Center (2)
- Monitoring (2)
- Network Management (4)
- Networking (3)
- NSI (1)
- nutanix (1)
- Observability (1)
- OT (1)
- Ransomware (2)
- SchoolTechnology (6)
- SD-WAN (1)
- SDN (1)
- securit (1)
- Security (77)
- security management (6)
- security strategy (9)
- SSE (2)
- sustainability (1)
- Telehealth (4)
- Telemedicine (1)
- veeam (1)
- Video (1)
- videoconferencing (1)
- Virtualization (2)
- VMware to Nutanix (1)
- webex (3)
- wifi (1)
- XDR (1)
- Zero Trust (8)


