VPN Crytography: Understanding It and Why It Matters
February 7, 2023 •Matt Tadevich

I frequently perform firewall upgrades from legacy Cisco devices. Oftentimes as we go through this process my customers need to upgrade their site-to-site VPNs from aging ciphers like DES and 3DES, or deprecated Diffie-Helman groups.
Background
Site-to-site VPNs are encrypted tunnels typically terminated between two network infrastructure devices (firewalls, routers) to extend connectivity between two specific remote networks.
IPsec (IP Security) is a suite of protocols used to create secure tunnels. One of the most common Security Association (SA) protocols within the IPsec suite is IKE (Internet Key Exchange), a key and encryption negotiating protocol that securely establishes the IPsec tunnel over 2 phases.
While there are two versions of IKE (IKEv1 and IKEv2), security best practices are to prefer IKEv2, as IKEv1 does not support all modern cryptographic tools that we will need (discussed later in this article).
IKEv2
IKEv2 was published in RFC5996 in 2010. IKEv2 provides the same function as IKEv1, however, it is more streamlined and much more secure. IKEv2 phase 1, known as the IKE_SA, creates a secure line of communication to exchange ESP (Encapsulating Security Payload) or AH (Authentication Header) Packets. IKE_SA configures several attributes that must match on both ends of the VPN for the Phase 1 Security Association (SA) to form. Those Attributes include the following:
- Encryption Algorithm (AES-GCM-256)
- Hashing (SHA-384 and SHA-512)
- Diffie-Helman (DH Groups 19, 20, 21)
- Psuedo-Random Function (SHA-384)
- Authentication Method (Shared Secret)
- Vendor-Specific Attributes (Optional)
Once Phase 1 is complete, Phase 2, also known as the CHILD_SA, begins to establish. Phase 2 sets up the IPSec Tunnel using either ESP within the Phase 1 tunnel. Phase 2 Attributes define the ESP configuration. In the instance of a Cisco Secure Firewall (formerly Cisco Firepower) they are the following:
- ESP Hash (SHA-256 or higher)
- ESP Encryption (AES-GCM-256)
- Perfect Forward Secrecy (Modulus Group 21)
Perfect Forward Secrecy (PFS) is an optional feature that utilizes Diffie-Helman to create temporary private key exchanges for each session, adding a layer of protection in the instance that session keys are compromised. Only the compromised session is affected.
You may have configured a VPN previously and seen cipher suites have cryptic names (e.g., AES-GCM-NULL-SHA). Let's investigate further.
Cryptography
Currently, best practices include what is known as the Commercial National Security Algorithm (CNSA), a suite of cryptographic ciphers that the NSA evolved out of their own NSA Suite B cryptology suite.
CMSA includes the following ciphers:
- Encryption: AES-GCM-256
- Hashing: NULL if using GCM encryption, otherwise, SHA-384 or SHA-512
- Key Exchange: Elliptic Curve Diffie-Helman using P-256 and P-384 curves (DH Groups 19, 20, and 21)
If a termination point in your VPN setup doesn’t support one or all of these attributes, it is recommended to go with the next best attributes such as:
- Encryption: AES-256
- Hashing: SHA-256
- Key Exchange: Diffie-Helman Group 14 or Higher, choosing the highest option available
Configuration Example:
Finally, as an example, are some screenshots of how you would create a Site-to-Site VPN on a Cisco Secure Firewall using the Commercial National Security Algorithm:
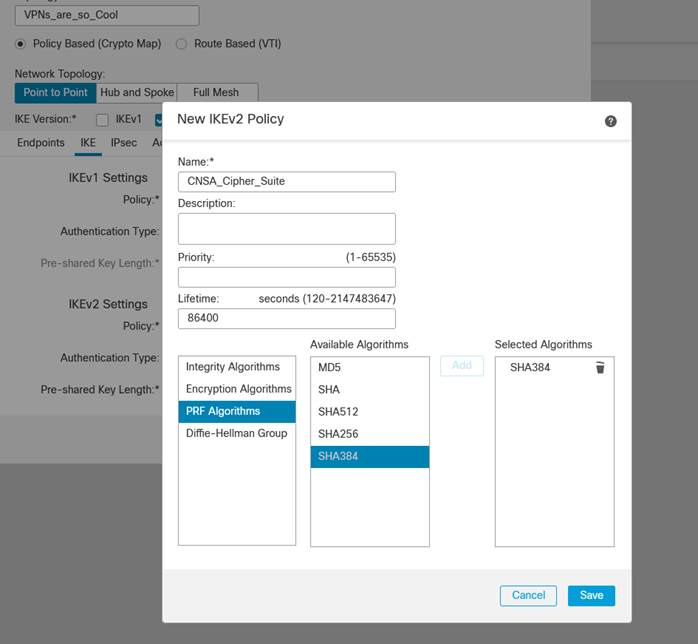
- After configuring the VPN-protected networks and termination IPs, we will configure the IKEv2 Policy. If you aren't sure which default Cipher Suite (AES-GCM-NULL-SHA) works for your situation, you can always (at least in the case of Cisco Firepower) create your own.
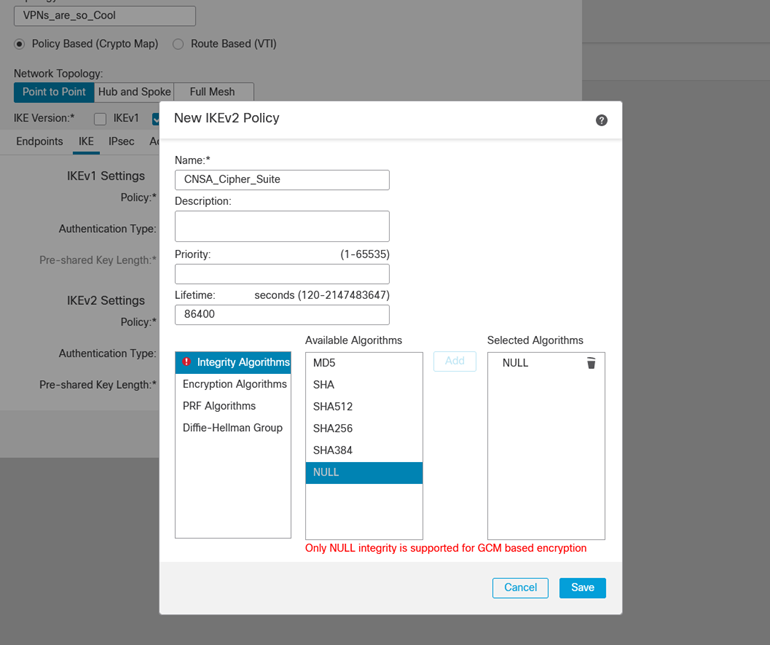
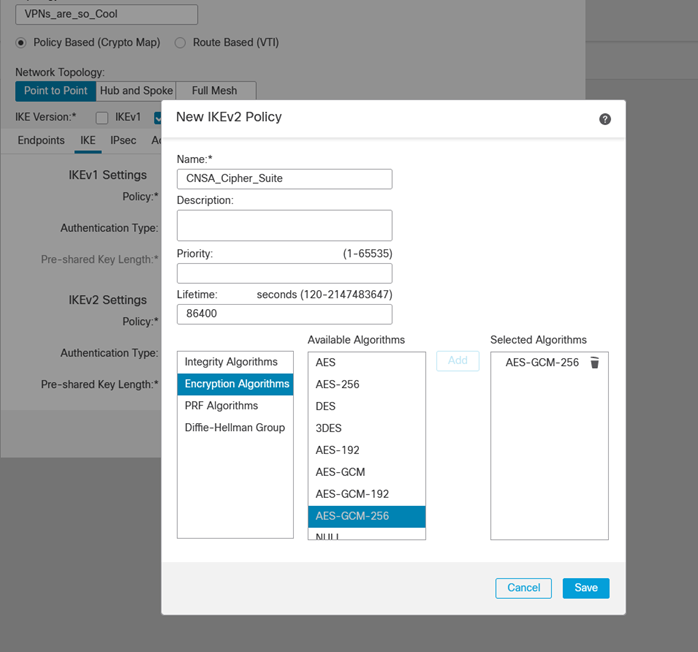
ii. Set Encryption to AES-GCM-256
iii. Set PRF to SHA384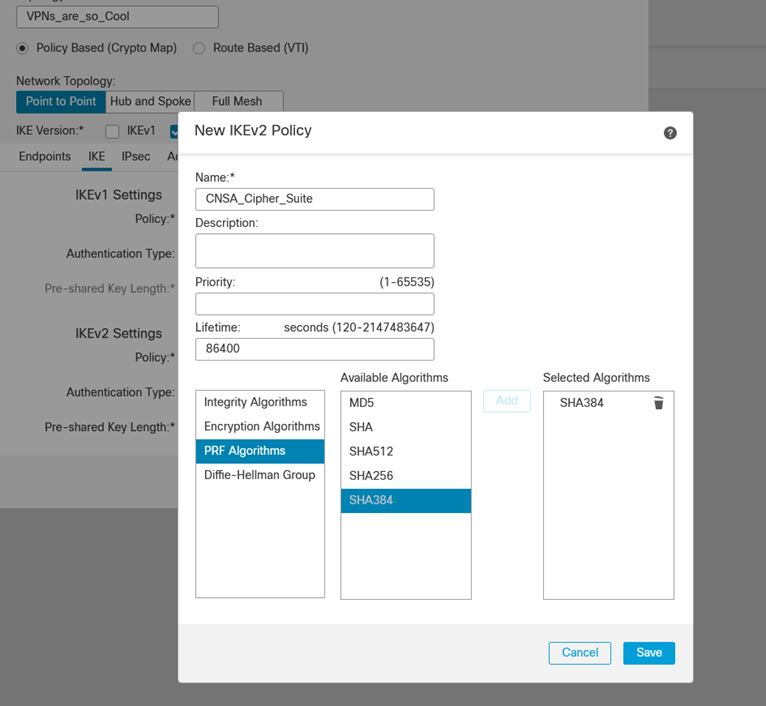
iv. Set Diffie-Helman to 21
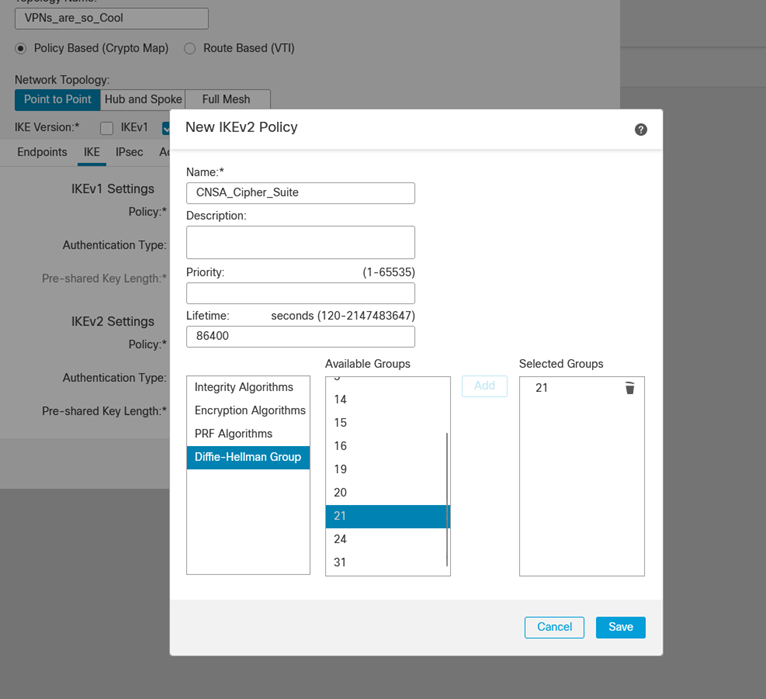
v. Set Perfect Forward Secrecy
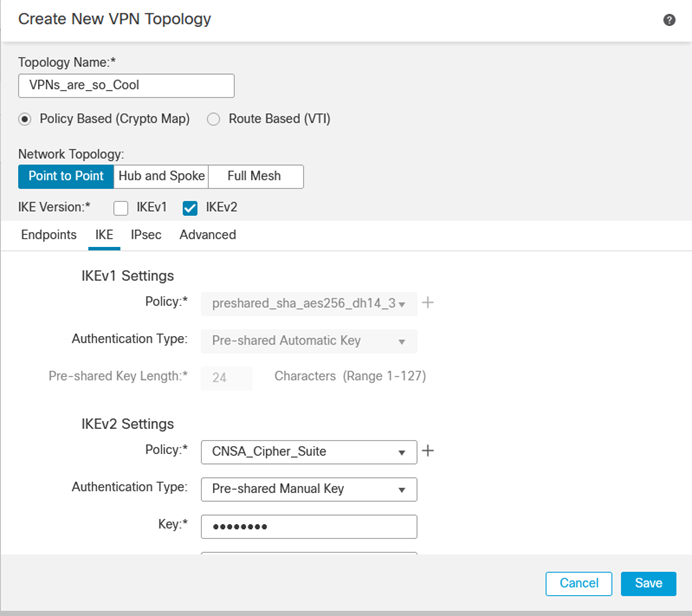
2. Once you have a IKEv2 Policy that is configured, you then need to set authentication to Pre-Shared Manual Key. Ideally using a password generator to ensure the key is robust.
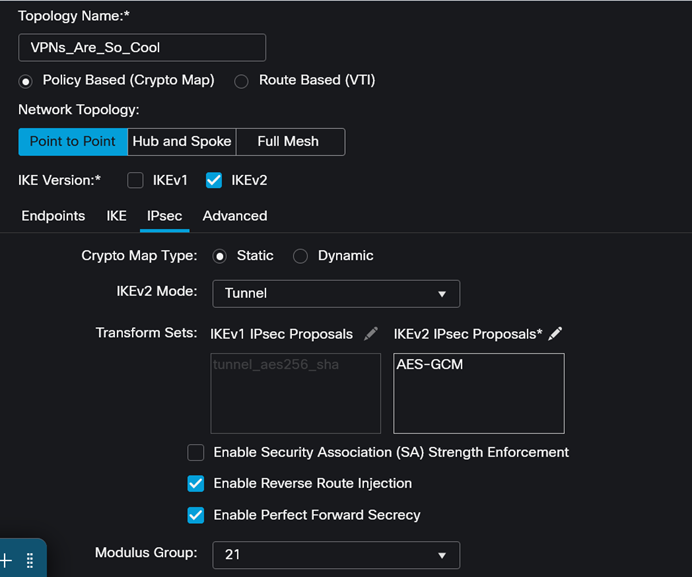
- You will then repeat that process for the IPSec Proposal, setting ESP Hash to Null and ESP Encryption to AES-GCM-256
Conclusion
To bridge everything together: VPN cryptography has evolved significantly over the last 20 years and is often misunderstood. Luckily, CNSA has provided us with a simple way to standardize a strong cryptographic posture. If you have further questions or happen to need network security services please reach out to the Network Solutions, Inc. (nsi1.com) Security Team!
Get Updates
Featured Articles
Categories
- AI (19)
- Automated Technology (10)
- backup (1)
- Cisco (33)
- Cisco Live Update (1)
- Cisco News (2)
- Cisco UCS (1)
- Cloud Networking (5)
- Collaboration (26)
- compute (1)
- CyberSecurity (36)
- Data Center (33)
- Defense (1)
- DevOps (3)
- DisasterRecovery (1)
- DNA (2)
- Education (3)
- Encryption (1)
- Enterprise Networking (34)
- Full-Stack (1)
- Future (1)
- healthcare (2)
- hybrid cloud (1)
- Hybrid Cloud Strategy (1)
- Hyperconverged Infrastructure (1)
- Infrastructure Cost Optimization (1)
- Innovation (1)
- Innovative Technology (12)
- Internet of Things (2)
- IoT (2)
- Managed Services (11)
- Manufacturing (1)
- Modern Data Center (2)
- Monitoring (2)
- Network Management (4)
- Networking (3)
- NSI (1)
- nutanix (1)
- Observability (1)
- OT (1)
- Ransomware (2)
- SchoolTechnology (6)
- SD-WAN (1)
- SDN (1)
- securit (1)
- Security (77)
- security management (6)
- security strategy (9)
- SSE (2)
- sustainability (1)
- Telehealth (4)
- Telemedicine (1)
- veeam (1)
- Video (1)
- videoconferencing (1)
- Virtualization (2)
- VMware to Nutanix (1)
- webex (3)
- wifi (1)
- XDR (1)
- Zero Trust (8)



